
Matteo Sordello, Zhiqi Bu, Jinshuo Dong · Privacy Amplification via Iteration for Shuffled and Online PNSGD · SlidesLive

High-speed and Large-scale Privacy Amplification Scheme for Quantum Key Distribution | Scientific Reports
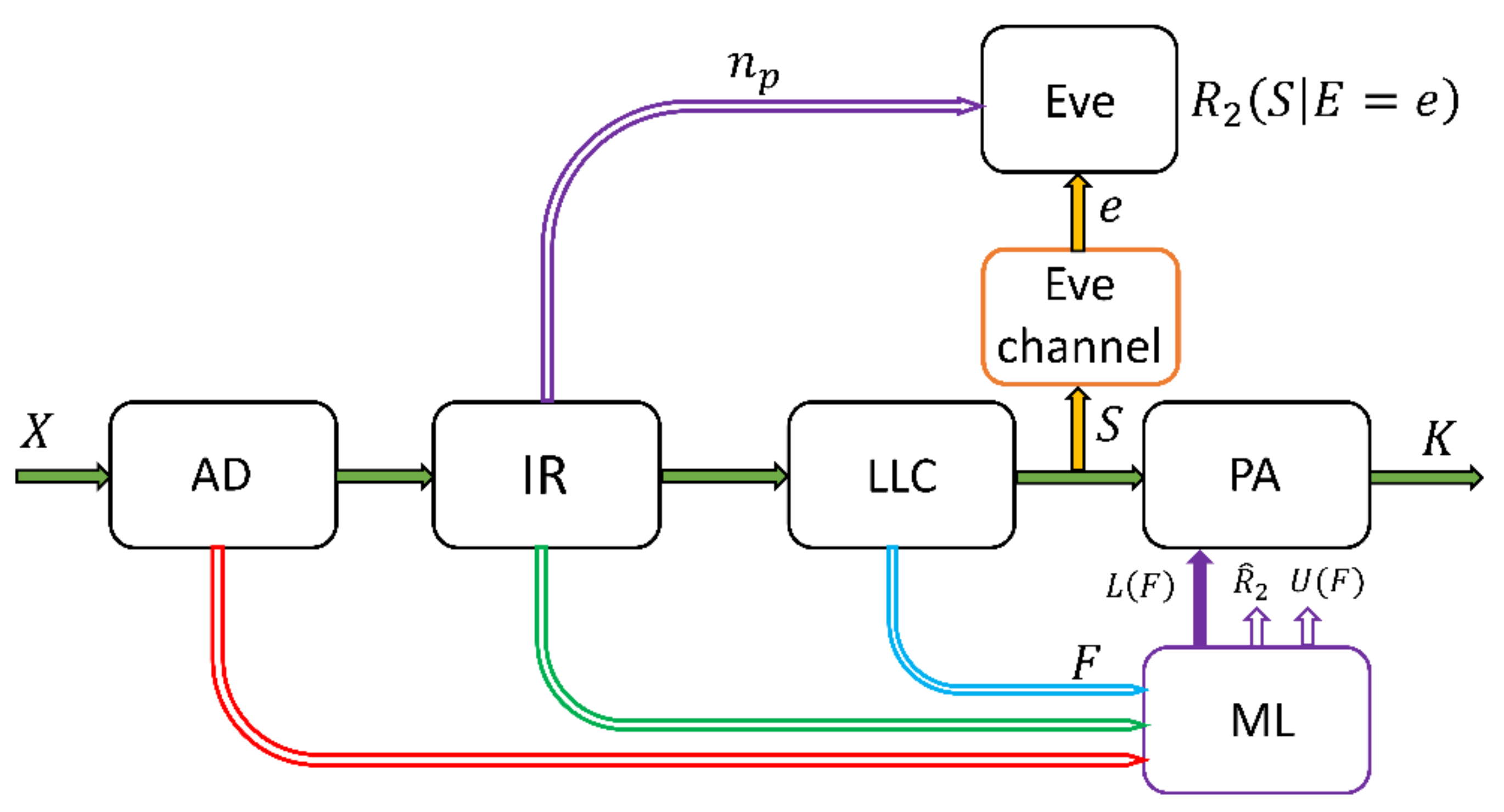
Symmetry | Free Full-Text | Privacy Amplification Strategies in Sequential Secret Key Distillation Protocols Based on Machine Learning

The process of length-compatible privacy amplification algorithm. The... | Download Scientific Diagram

Vitaly 🇺🇦 Feldman on X: "IMO the most significant recent development in privacy preserving data analysis are systems and models that use an anonymizing shuffler. However their formal analysis was rather involved

The process of length-compatible privacy amplification algorithm. The... | Download Scientific Diagram
All optical metropolitan quantum key distribution network with post-quantum cryptography authentication
![PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5ab3cb538f80f4bbf539103464fe597ba2d93a7c/1-Figure1-1.png)
PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar
![PDF] High-speed Implementation of FFT-based Privacy Amplification on FPGA in Quantum Key Distribution. | Semantic Scholar PDF] High-speed Implementation of FFT-based Privacy Amplification on FPGA in Quantum Key Distribution. | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/00d9158399761b85815dfddbff75a1e12d55017c/3-Figure1-1.png)
PDF] High-speed Implementation of FFT-based Privacy Amplification on FPGA in Quantum Key Distribution. | Semantic Scholar
High-Speed Implementation of Length-Compatible Privacy Amplification in Continuous-Variable Quantum Key Distribution

Privacy Amplification with Couplings and Overlapping Mixtures | Rafik Hariri Institute for Computing and Computational Science & Engineering

PPT - Randomness Extraction and Privacy Amplification with quantum eavesdroppers PowerPoint Presentation - ID:4846836
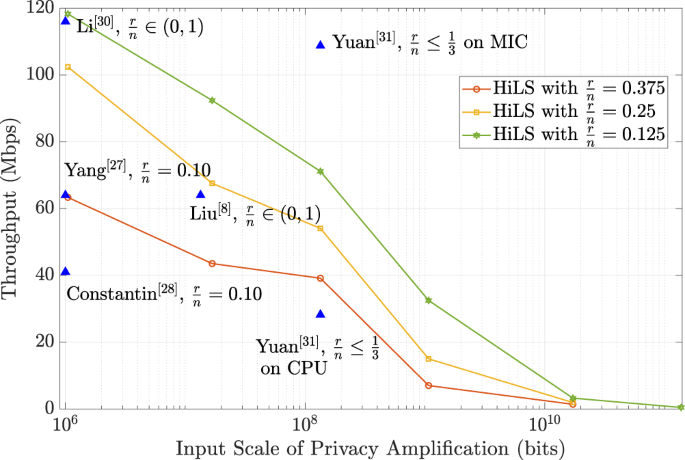
High-speed and Large-scale Privacy Amplification Scheme for Quantum Key Distribution | Scientific Reports
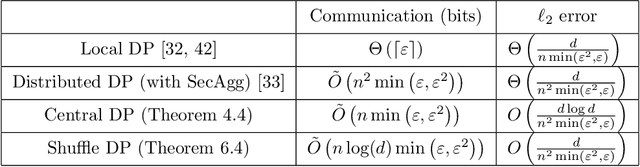
Privacy Amplification via Compression: Achieving the Optimal Privacy-Accuracy-Communication Trade-off in Distributed Mean Estimation: Paper and Code - CatalyzeX
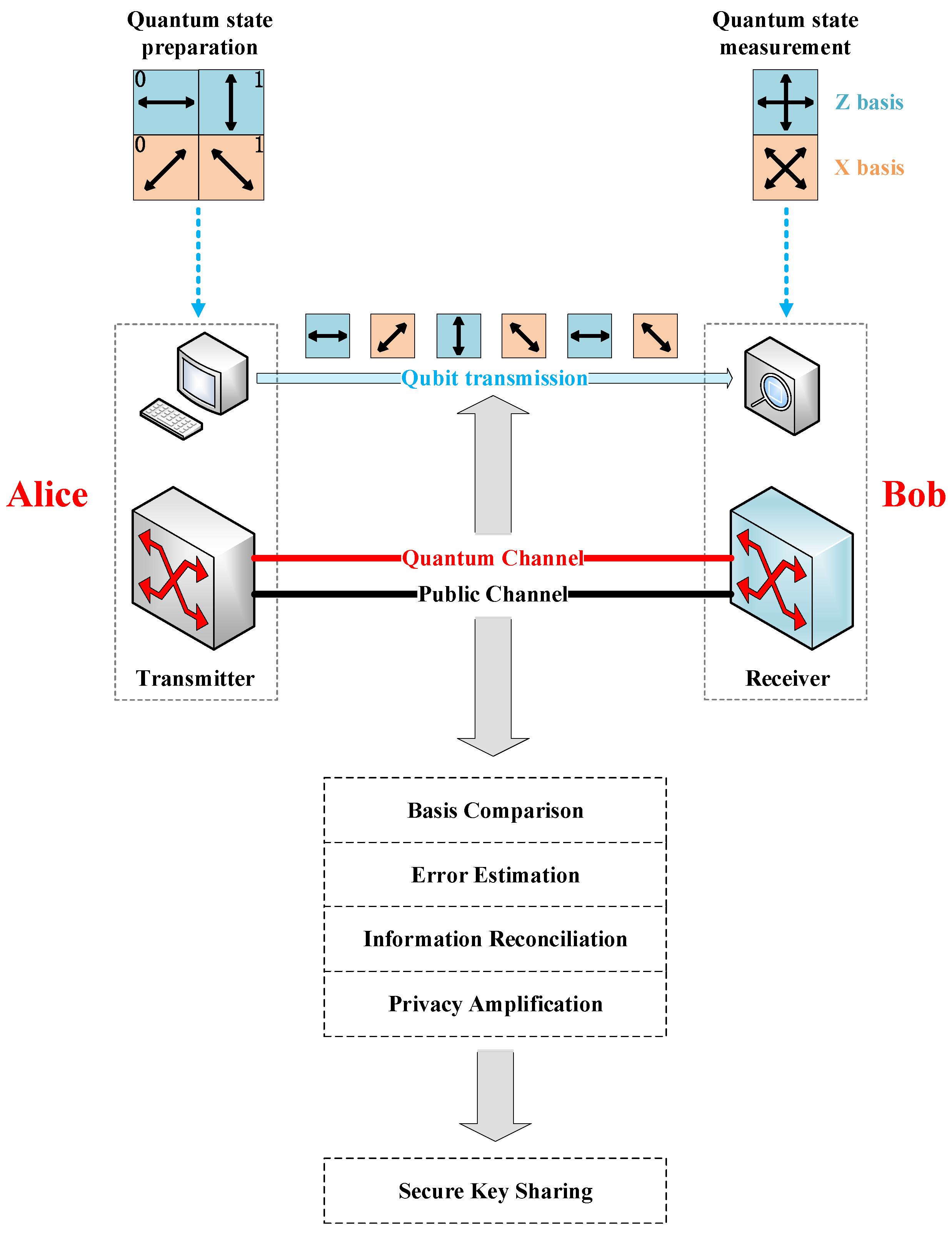
Entropy | Free Full-Text | A Resource-Adaptive Routing Scheme with Wavelength Conflicts in Quantum Key Distribution Optical Networks










